2. Enabling or Disabling a User for RWA
You can enable or disable the access of individual users to RWA. Normally, all users are enabled for RWA, but if you want only a
subset of your users to have the privilege to log in to RWA you can
disable the access of those you want to exclude.
Follow these steps to enable or disable a user from Remote Web
Workplace:
Open the Windows SBS Console if it isn’t already
open.
Click on Users And Groups in the navigation bar and then
click on the Groups tab.
Select the Windows SBS Remote Web Access Users security
group in the main pane, and click Edit Group Properties in the
Tasks pane to open the Properties dialog box for the group, as
shown in Figure 12.
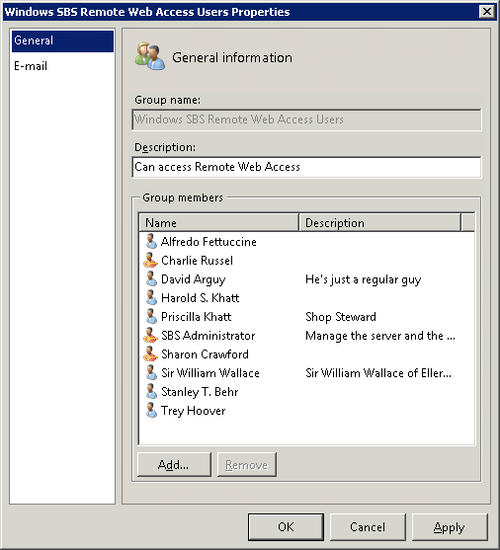
Select a user account in the Group Members pane, and click
Remove to remove the user.
To add a user account, click Add to open the Change Group
Membership dialog box shown in Figure 13.
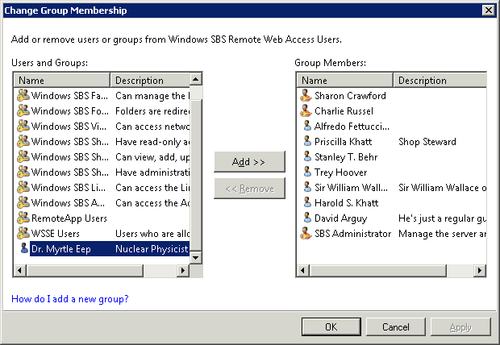
Select one or more users or groups in the left pane, and click Add to
add them to the group. To remove users from the group, select them in the right
pane and click Remove.
Click OK and then OK again to exit the dialog box and
return to the Windows SBS Console.
Note:
If your environment includes multiple users who should not
have permission to use Remote Web Access, consider creating a User
Role for them that excludes membership in the Windows SBS Remote
Web Access Users security group. This is a better way to manage
the rights and privileges of multiple users in a consistent
way.
Remote Web Access is a secure way to connect to your SBS
network. It uses IPSec tunneling, and it uses the authentication
of Microsoft’s Active Directory (your user name and password) to
grant access to the resources of your SBS network. That being
said, if your SBS network contains sensitive information and
you’re subject to regulatory requirements for data protection, you
should consider Two Factor Authentication (TFA) on RWA, especially for any accounts that are either
Network Administrators or have special access to sensitive
data.
Authentication is the process of ensuring that the
individual who requests access to a resource is, in fact, the
individual she is claiming to be. There are four basic kinds of
authentication: “what-you-know,” “who-you-are,” “what-you-have,”
and “where-you-are.” TFA requires that any user requesting remote access
to the resources of your SBS network use two methods to uniquely
identify herself. The first method is the providing the user name
and password of the user, and the second is some other factor. The
real beauty of TFA is that even if one of your factors is
compromised, it’s useless without the second factor.
The basic user name and password is a what-you-know factor,
and it’s the most commonly used form of authentication. When
combined with a sort of loose where-you-are factor—that is, at the
console of your own PC—and when passwords or passphrases are
sufficiently complex, it’s a good method of authentication.
Who-you-are authentication is usually some form of biometric
analysis—fingerprint readers, retina scanners, and even visual
recognition software all are forms of who-you-are authentication.
We’re not big fans of the most common of these, fingerprint
readers. They’re rather easily defeated from what we’ve seen to
date.
What-you-have authentication is usually something like a
smart card or a one-time password generator. Microsoft’s corporate
network uses smart cards for its TFA, but we think one-time
passwords are a lot easier to deal with and deploy in a small
business. You don’t require deploying smart card readers for
everyone, and the overall costs are significantly less as a
result.
Finally, where-you-are authentication uses your physical
location as a proof of who you are. An example is the variable
authentication process that some banks are implementing. It starts
with the IP address and machine name from which you’re connecting
to your bank. The bank knows that the IP address is typical for
you and only asks a standard set of verification questions. But if
you were to connect from a public wireless access point while
you’re on vacation, the bank would immediately be more cautious
about who you are claiming to be, and the secondary verification
process is more detailed. This kind of variable authentication
process is expensive to implement and outside the scope of most
small businesses.
We use TFA for remote access to our SBS network. We’ve
implemented Scorpion Software’s AuthAnvil (http://www.scorpionsoft.com). The AuthAnvil RWA agent (formerly known as RWWGuard)
extends the standard RWA logon page to require a one-time password, as
shown in Figure 14.
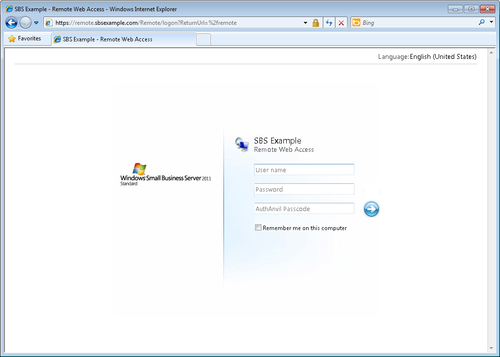
What we really like about AuthAnvil is that it’s almost
completely transparent. It looks and feels just like SBS, except
for the one additional field for our one-time password. And with
the AuthAnvil Soft Token running on our phone, we no longer even
have to carry around an AuthAnvil key fob passcode
generator.