2. Enabling Access with a Sharing Router
If
you use a connection-sharing router on your LAN, you need to follow a
somewhat different procedure to enable outside access to services on
your network.
You must still open Windows
Firewall on the computer(s) providing services, as described in the
first six-step procedure in the previous section. Then you must use a
manufacturer-specific procedure to set up forwarding for services that
you want to expose to the Internet.
One
difficulty with these devices is that you must forward services by IP
address, not by computer name, and, normally, you set up computers to
obtain their IP addresses automatically. This makes the computers
moving targets because their IP address could change from day to day.
You
have to make special arrangements for the computers on your LAN that
you want to use to host services. On your router’s setup screens, make
a note of the range of IP addresses that it will hand out to computers
requesting automatic configuration. Most routers have a place to enter
a starting IP address and a maximum number of addresses. For instance,
the starting number might be 2, with a limit of 100 addresses. For each
computer that will provide an outside service, pick a number between 2
and 254 that is not in the range of
addresses handed out by the router, and use that as the last number in
the computer’s IP address. I recommend using address 250 and working
downward from there for any other computers that require a static
address.
To configure the computer’s network address:
For setting up Remote Desktop, with protocol TCP
port 3389. You’ll need to use the protocol and port numbers for the
service you’re enabling.
Use a static IP
address ending with .250 for the first computer you set up to receive
incoming connections. Use .249 for the second computer, and work
downward from there. Be sure to keep a list of the computers you assign
static addresses to, and the addresses you assign.
For
services that use TCP/UDP in unpredictable ways, you must use another
approach to forwarding on your LAN. Some services, such as Windows Live
Messenger, communicate their private,
internal IP address to the computer on the other end of the connection;
when the other computer tries to send data to this private address, it
fails. To use these services with a hardware router, you must enable
UPnP.
Other
services use network protocols other than TCP and UDP, and most routers
can’t be set up to forward them. Incoming Microsoft VPN connections
fall into this category. Some routers have built-in support for
Microsoft’s PPTP protocol. If yours has this support, your router’s
manual will tell you how to forward VPN connections to a host computer.
Otherwise, to support nonstandard services of this sort, you have to tell the router to forward all
unrecognized incoming data to one designated computer. In effect, this
exposes that computer to the Internet, so it’s a fairly significant
security risk. In fact, most routers call this targeted computer a DMZ
host, referring to the notorious Korean no-man’s-land called the
Demilitarized Zone and the peculiar danger one faces standing in it.
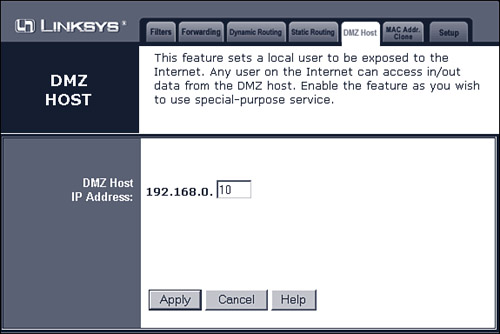
To
enable a DMZ host, you want to use a fixed IP address on the designated
computer, as described in the previous section. Use your router’s
configuration screen to specify this selected IP address as the DMZ
host. The configuration screen for my particular router is shown in Figure 5; yours might differ.
Now,
designating a DMZ host means that this computer is fully exposed to the
Internet, so you must protect it with a firewall of some sort. On this
computer, you must set its network location to Public Network.
Tip
It’s not a bad idea to enable filtering for these ports even if you’re not using a DMZ host. It’s essential to do this if you set up a DMZ host. |
You should also set up filtering in your router to block ports 137–139 and 445. Figure 6 shows how this is done on my Linksys router; your router might use a different method.