3.3 Implementing EFS
Putting EFS in place requires a series of operations:
Find out if savvy users are already using EFS on their own.
Put the GPO settings required to enable EFS in place.
Prepare your data recovery agents (DRA).
Have your users use two-factor authentication to remove their certificate from the machine they work with.
Inform your users of the EFS policy you put in place and their responsibilities in relation to this policy.
Begin
with the identification of who may be using EFS already. Savvy users
can already have enabled standalone EFS on their own. If this happens,
then you'll need to use a special approach for them. If you're working
on this before anyone uses EFS, then you're lucky. All you need to do
is disable standalone EFS through Group Policy. But if some of your
users already use EFS, then you'll have to first disable EFS for those
who are not using it, and then migrate the ones who are to the
centrally controlled EFS policy. Do not disable EFS on the systems
where it is already in use because your users will lose access to their
data. To find out who is using EFS, use the following command line in a
logon script:
Cipher /U /N >\\servername\sharename\%username%.txt
Basically,
you use the cipher command to identify if users are running EFS and you
are piping the result into a file named with the user name and placing
the file on a central share somewhere in your network. Then, you can
use the results to generate a Security group in AD, for example, a
group named Standalone EFS Users, to contain the users who are already
using EFS.
Now you're ready to prepare the
GPO. If you do not have any users already using EFS, then you can make
these GPO changes in the same GPO that you used for folder redirection
earlier. If you do, then you have to create a new GPO. Use either of
the two following procedures. You will need Group Policy Modification
privileges to make these changes.
For organizations that are not yet using EFS:
Launch the Group Policy Management Console.
Locate the User Profile Management GPO and right-click to select Edit. You use this GPO because the settings you need to modify will apply to computer objects.
Navigate to Computer Configuration =>
Policies =>
Windows Settings =>
Security Settings =>
Public Key Policies =>
Encrypting File System.
Right-click on Encrypting File System and select Properties.
On the General tab, set the policy to Don't allow. Click OK to enable the policy and close GPEdit.
Remember to update your GPO description to reflect that it is also used for EFS.
For organizations that have users running EFS, use the following procedure:
Create a new policy. You must create a new policy because you will be preventing the users who are already using EFS from using this policy.
Right-click the target OU containing PCs, select Create a GPO in this domain, and link it here.
Name the policy appropriately and click OK. For example, you can name it Deny EFS Policy.
Now, right-click the new policy link and select Edit.
Choose Computer Configuration =>
Policies =>
Windows Settings =>
Security Settings =>
Public Key Policies =>
Encrypting File System.
Right-click Encrypting File System and select Properties.
On the General tab, set the policy to Don't allow.
Click OK to enable the policy and close GPEdit.
Now filter this policy with the security group you created earlier.
Move
to the Delegation tab for the policy in the GPMC, click Add to select
the Standalone EFS Users group, and assign the Read property to them.
Next,
click Advanced, deselect Allow Read, and select Deny Read for the
Standalone EFS Users group. This blocks them from reading this policy.
Now
that no users can use EFS except those that already have it. Because
you elected to enroll users without any user input in the preparation
of your EFS certificate template, and especially if you elected to
automatically enroll users, everyone should have received a new
certificate by now. This means you can assign a script to the
Standalone EFS Users group to update their files with the new
certificate. Run the following command in your script:
Cipher /U >\\servername\sharename\%username%.txt
This
command automatically updates all of the standalone EFS certificates in
pre-encrypted files to the new, centrally controlled certificate. It is
a good idea to add a user count in the script, such as the generated
text file to ensure that you know when all files have been updated for
each user.
Now you're ready to define your central EFS policy.
Begin by launching the Group Policy Management Console.
If you had standalone users, begin by deleting the Deny EFS Policy you
created earlier, and then proceed to Step 5. If not, go to the next
step.
Locate the User Profile Management GPO and right-click on it to select Edit.
Move to Computer Configuration =>
Policies =>
Windows Settings =>
Security Settings =>
Public Key Policies =>
Encrypting File System.
Right-click on Encrypting File System and select Properties. On the General tab, select Not Defined and close GPEdit. Doing this turns off the EFS blockage you put in place earlier.
If
you only want to apply EFS to mobile systems, then return to GPMC and
right-click on the OU that contains mobile PCs to select Create a GPO
in this Domain, and Link it here. Name the GPO EFS Policy, then
right-click on the link to select Edit. If you want to assign EFS to
all systems, then locate the User Profile Management GPO and
right-click on it to select Edit.
Move to Computer Configuration =>
Policies =>
Windows Settings =>
Security Settings =>
Public Key Policies =>
Encrypting File System.
Right-click on Encrypting File System and select Properties.
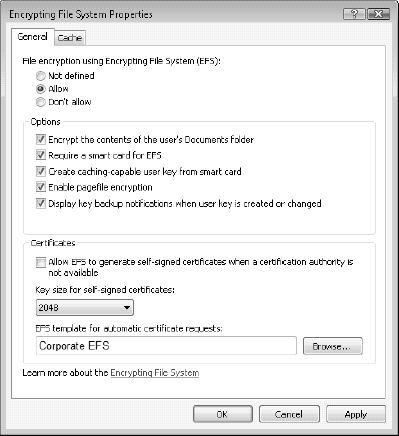
On the General tab, apply the following settings (see
Figure 4):
Set the policy to Allow.
Select Encrypt the contents of the user's Documents folder.
Select Require smart card for EFS.
Leave Create caching-capable user key from smart card selected.
Select Enable pagefile encryption.
Select Display key backup notifications when user key is created or changed.
Uncheck Allow EFS to generate self-signed certificates when a certification authority is not available.
Use the Browse button to locate your Corporate EFS template.
On the Cache tab, leave the Cache timeout option selected and select User locks workstation.
Click OK to enable the policy.
Now move to the Computer Configuration =>
Policies =>
Administrative Templates =>
Network =>
Offline Files section.
Double-click the Encrypt the Offline Files cache setting and Enable it. Click OK to close it. Close GPEdit for now.
This
policy enables EFS on all of the computers in the target OU. It will
automatically encrypt the Documents folder as well as the pagefile and
all data in the offline cache. But, as you know, some data will not be
covered by this policy. For example, data that is contained within the
AppData\Local and AppData\LocalLow folders will not be encrypted. If
your users are running Microsoft Outlook, then it is possible that
e-mail messages and personal stores are not protected. To ensure that
all sensitive data is protected, you should supplement this policy with
a logon script that targets all systems that should include encrypted
data and includes the following command:
Cipher /e /s /a "%userprofile%\appData\Local
Cipher /e /s /a "%userprofile%\appData\LocalLow
This
command ensures that all data is protected on the target systems. All
other data folders are in the offline cache because of folder
redirection.