A big part of keeping any computer secure
involves examining what users do with the computer. For Windows Home
Server, this means tracking events such as logon failures (repeated
failures might indicate a malicious user trying different passwords)
and account changes (in which someone changes some aspect of a user
account). This type of tracking is called auditing.
Note
Since
Windows Home Server 2011 is built upon Windows Server 2008 R2, you see
the same auditing policies as you would if you were working with a pure
Windows Server 2008 R2 system. However, there are many Windows Server
2008 R2 auditing policies that don’t apply to Windows Home Server; for
example, it’s useless to audit accesses to Active Directory (AD)
objects because Windows Home Server doesn’t support AD.
In the next section, I show you how to enable the
security auditing policies in Windows Home Server, and then I explain
how to track auditing events.
1. Activating the Auditing Policies
To enable Windows Home Server’s security auditing policies, follow these steps:
1. | Log on to Windows Home Server.
|
2. | Select Start, Administrative Tools, Local Security Policy. The Local Security Policy window appears.
Tip
You can also open the Local Security Settings window by selecting Start, typing secpol.msc, and pressing Enter.
|
3. | Open the Local Policies branch, and click Audit Policy. Windows Home Server displays the audit policies, as shown in Figure 1.
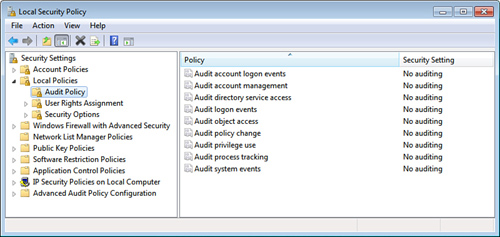
|
4. | Double-click the policy you want to work with.
|
5. | If you want to know when someone uses the policy event successfully, activate the Success check box.
|
6. | If you want to know when someone uses the policy event unsuccessfully, activate the Failure check box.
|
7. | Click OK.
|
8. | Repeat steps 4–7 for the other events you want to audit.
|