2. Understanding the Auditing Policies
To help you decide which auditing policies to use,
the next few sections give you a bit of detail about some of them. Note
that several of these policies require AD to return meaningful or
useful results. This means they don’t apply to Windows Home Server, so
I don’t discuss them here.
Audit Account Logon Events
The Audit Account Logon Events policy enables you to
track when users log on to their account on the Windows Home Server
computer. If you track failures for this policy, the resulting Failure
Audit event returns an Error Code value, as shown in Figure 2. Table 1 tells you what the various error codes mean.
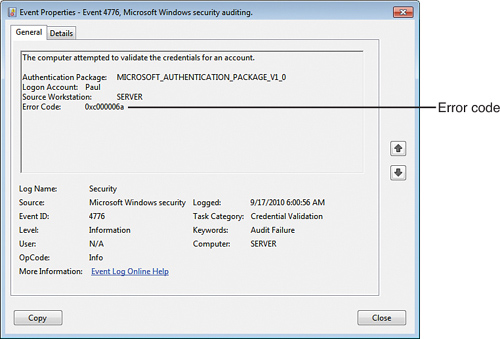
Table 1. Error Codes Returned for Account Logon Failure Events
| Error Code | Description |
|---|
| 0xC0000064 | The user tried to log on with a misspelled or invalid username. |
| 0xC000006A | The user tried to log on with a misspelled or invalid password. |
| 0xC000006D | The user tried to log on with an unknown username or bad password. |
| 0xC000006F | The user tried to log on outside the account’s authorized hours. |
| 0xC0000070 | The user tried to log on from an unauthorized computer. |
| 0xC0000071 | The user tried to log on with an expired password. |
| 0xC0000072 | The user’s account is disabled. |
| 0xC0000193 | The user’s account is expired. |
| 0xC0000224 | The user was supposed to change his password at the next logon, but he didn’t. |
| 0xC0000234 | The user’s account is locked. |
Audit Account Management
The
Audit Account Management policy enables you to track events related to
managing groups and user accounts on Windows Home Server. Events
include creating new groups or users, modifying or deleting groups or
users, changing user passwords, or renaming or disabling users. Table 2 lists the possible event IDs for the Audit Account Management category.
Table 2. Event ID Values for Account Management Events
| Account Management Event ID | Description |
|---|
| 4720 | A user account was created. |
| 4722 | A user account was enabled. |
| 4723 | An attempt was made to change an account’s password. |
| 4724 | An attempt was made to reset an account’s password. |
| 4725 | A user account was disabled. |
| 4726 | A user account was deleted. |
| 4727 | A security-enabled global group was created. |
| 4728 | A member was added to a security-enabled global group. |
| 4729 | A member was removed from a security-enabled global group. |
| 4730 | A security-enabled global group was deleted. |
| 4731 | A security-enabled local group was created. |
| 4732 | A member was added to a security-enabled local group. |
| 4733 | A member was removed from a security-enabled local group. |
| 4734 | A security-enabled local group was deleted. |
| 4735 | A security-enabled local group was changed. |
| 4737 | A security-enabled global group was changed. |
| 4738 | A user account was changed. |
| 4739 | Domain Policy was changed. |
| 4740 | A user account was locked out. |
| 4741 | A computer account was created. |
| 4742 | A computer account was changed. |
| 4743 | A computer account was deleted. |
| 4754 | A security-enabled universal group was created. |
| 4755 | A security-enabled universal group was changed. |
| 4756 | A member was added to a security-enabled universal group. |
| 4757 | A member was removed from a security-enabled universal group. |
| 4758 | A security-enabled universal group was deleted. |
| 4765 | SID History was added to an account. |
| 4766 | An attempt to add the Security ID (SID) History to an account failed. |
| 4767 | A user account was unlocked. |
| 4780 | The Access Control List (ACL) was set on accounts that are members of administrators groups. |
| 4781 | The name of an account was changed. |
| 4782 | The password hash for an account was accessed. |
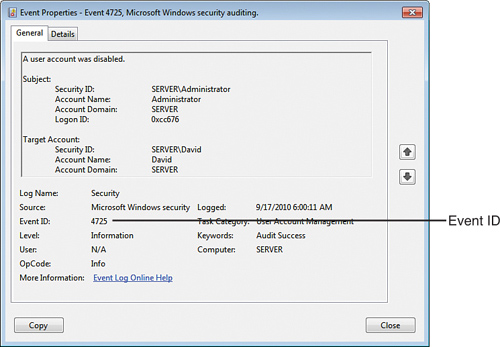
Figure 3 shows a sample event that occurred when a user’s account was disabled (event ID 4725).
Audit Logon Events
The Audit Logon Events policy enables you to track
when users log on to the Windows Home Server network. These events
always occur in conjunction with Account Logon events. That is, first
Windows Home Server processes the logon to the user’s account on the
server; then it processes the logon to the network. Table 3 lists the possible event IDs for the Audit Logon Events category.
Table 3. Event ID Values for Logon Events
| Logon Event ID | Description |
|---|
| 4624 | An account was successfully logged on. |
| 4625 | An account failed to log on. |
| 4634 | An account was logged off. |
| 4647 | A user initiated logoff. |
| 4648 | A logon was attempted using explicit credentials. |
| 4649 | A replay attack was detected. |
| 4675 | SIDs were filtered. |
| 4778 | A session was reconnected to a window station. |
| 4779 | A session was disconnected from a window station. |
| 4800 | The workstation was locked. |
| 4801 | The workstation was unlocked. |
| 4802 | The screensaver was invoked. |
| 4803 | The screensaver was dismissed. |
| 5378 | The requested credentials delegation was disallowed by policy. |
| 5632 | A request was made to authenticate to a wireless network. |
| 5633 | A request was made to authenticate to a wired network. |
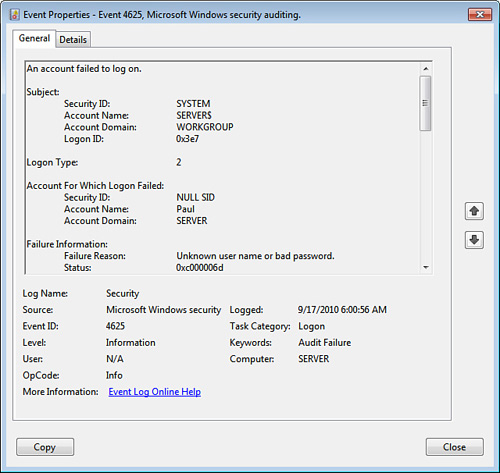
If you’re auditing failures for this category, each Failure Audit event tells you the reason for the failure, as shown in Figure 4.
Audit Policy Change
The Audit Policy Change policy enables you to track
when users make changes to group policies. The resulting event shows
you what policy was changed and what the new policy setting is. For
example, Figure 5 shows an event generated by modifying the auditing policies.

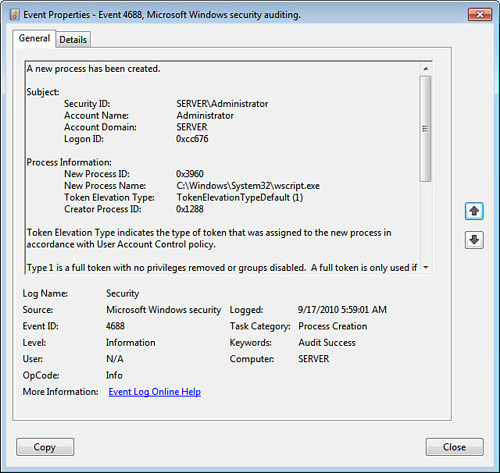
Audit Process Tracking
The Audit Process Tracking policy enables you to
track the starting and stopping of processes, including programs. For
example, you might want to track when scripts run on the server. Most
scripts are handled by wscript.exe, so the program runs each time a script is launched. Figure 6 shows an example event created when a script starts.
Audit System Events
The Audit System Events policy enables you to track
system events such as shutdown and startup, security changes, and
system time changes. Figure 7 shows an example event, and Table 4 lists the possible event IDs.
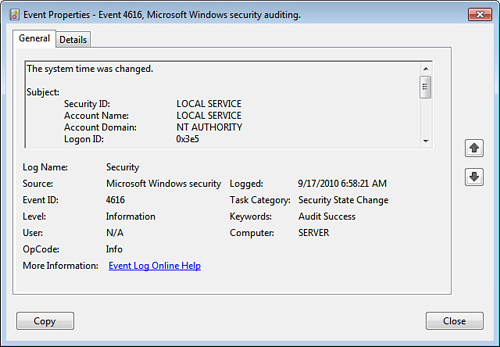
Table 4. Event ID Values for System Events
| System Event ID | Description |
|---|
| 4608 | Windows is starting up. |
| 4609 | Windows is shutting down. |
| 4616 | The system time was changed. |
| 4618 | A monitored security event pattern has occurred. |
| 4621 | The
administrator recovered the system from CrashOnAuditFail. Users who are
not administrators will now be allowed to log on. Some auditable
activity might not have been recorded. |
| 4697 | A service was installed in the system. |
| 5024 | The Windows Firewall Service has started successfully. |
| 5025 | The Windows Firewall Service has been stopped. |
| 5027 | The
Windows Firewall Service was unable to retrieve the security policy
from the local storage. The service will continue enforcing the current
policy. |
| 5028 | The
Windows Firewall Service was unable to parse the new security policy.
The service will continue with currently enforced policy. |
| 5029 | The Windows Firewall Service failed to initialize the driver. The service will continue to enforce the current policy. |
| 5030 | The Windows Firewall Service failed to start. |
| 5032 | Windows
Firewall was unable to notify the user that it blocked an application
from accepting incoming connections on the network. |
| 5033 | The Windows Firewall Driver has started successfully. |
| 5034 | The Windows Firewall Driver has been stopped. |
| 5035 | The Windows Firewall Driver failed to start. |
| 5037 | The Windows Firewall Driver detected a critical runtime error. |
| 6008 | The previous system shutdown was unexpected. |