2. Setting Security and Privacy Preferences
In
many ways, the Web is a safer place than the “real” world, but it does
present its own unique dangers. The greatest hazards involve sensitive
and private information about you or your company being compromised, or
having your computer infected with a software virus. IE8 incorporates a
number of security features to protect you from these hazards, and you
can customize those features to suit your own needs, browsing habits,
and company policies.
Begin by clicking
the Tools button and opening the Internet Options dialog box. Click the
Security tab. Click Default Level in the lower-right corner of the
dialog box to show the slider that allows you to set a security level
for each zone, as shown in Figure 4.
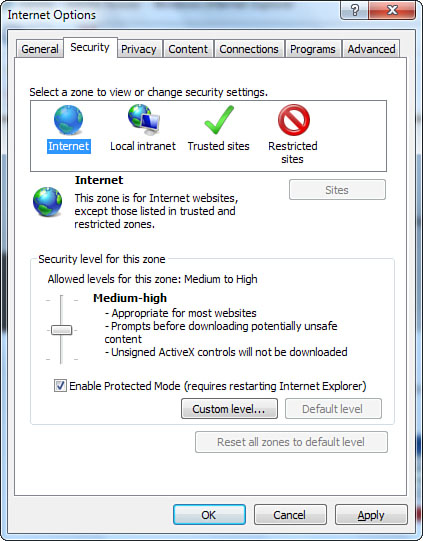
You first need to select a zone for which you want to customize settings. Figure 4 shows the four zones, described here:
Internet— This zone applies to all resources outside your LAN or intranet.
Local Intranet—
This zone applies to pages available on your company’s intranet. These
pages are usually more trustworthy and can justify less-restrictive
settings.
Trusted Sites—
You manually designate these sites as trusted. To designate a trusted
site, browse to the site, open this dialog box, select the Trusted
Sites zone, and click Sites. Here you can add the site to your Trusted
Sites zone list. Trusted sites usually allow lighter security.
Restricted Sites—
Designated in the same manner as Trusted Sites, websites listed here
are ones you specifically find untrustworthy. They should have the
strictest security settings.
Caution
Before
you designate a web page as trusted, remember that even the most
diligently maintained sites can be compromised. Recent “hacker” attacks
at websites of the FBI, U.S. Army, and others might make you question
the practice of designating any website as “trustworthy.” |
Each
zone has its own security preferences that you can set. The easiest way
to set preferences is to choose one of the three basic levels offered
in the dialog box. The default level is Medium, and for most web users,
this setting works best because it provides a good balance of security
and usability. The High setting offers the greatest possible security,
but you might find that the level is so restrictive that it’s difficult
to browse your favorite websites.
In
contrast, the Medium and Medium-Low levels make browsing much easier
because you aren’t presented with dialog boxes and warnings every time
a potentially hazardous activity begins. Because these two levels leave
too many doors open to virus infection and other dangers, they are not
advisable in most situations.
Besides
setting a basic security level, you can customize individual settings.
First, choose a basic level (such as Medium) and then try these steps:
1. | Click Custom Level to open the Security Settings dialog box, shown in Figure 5.
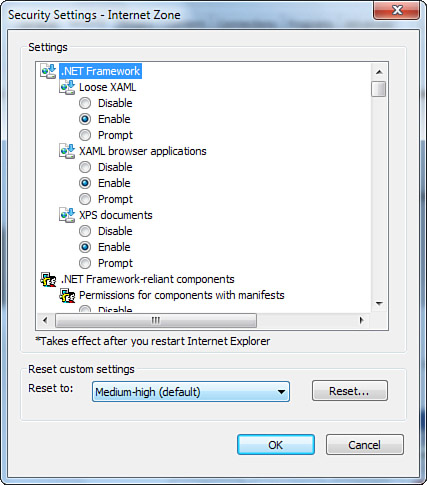
|
2. | Browse the list of options and apply custom settings as you see fit.
|
3. | Click OK when you’re finished. A Warning dialog box appears, asking whether you really want to apply the changes. Choose Yes.
|
Review
the items in the Security Settings dialog box that pertain to ActiveX
controls and Java applets. Assess these settings carefully, especially
those for ActiveX controls, because of the unique hazards they can
present. The ActiveX standard contains loopholes, so unsigned controls
can run virtually any OLE-compliant operation on your system. Java, on
the other hand, is relatively—but not entirely—secure.
You
should also consider your desired level of cookie security. Because
cookies are text only, they cannot contain a virus or other harmful
content. However, they can contain personal information, such as a
record of web pages you have visited, how long you spent at a page, how
many times you have visited, personal preferences for a web page, and
even user IDs and passwords. For these reasons, many people regard
cookies as an invasion of privacy.
You can
disable cookies, or you can choose to have IE prompt you every time a
site attempts to leave a cookie in your cache. However, keep in mind
that some websites make such heavy use of cookies that you could find
it difficult—if not impossible—to browse the Web normally.
To
set your cookie preferences, click the Tools button, click Internet
Options, and then click the Privacy tab. The Settings area enables you
to determine how and when cookies are sent. Choose a level you are
comfortable with, or click the Advanced button to select the Override
Automatic Cookie Handling option and specify whether IE will always
accept, block, or prompt you before enabling first-party or third-party
cookies.
You
might want to override your normal cookie settings for certain
websites. If so, go to the Websites area of the Privacy tab and click
the Edit button. In the text box, enter a complete website address.
Then click the Block or Allow button to specify websites for which you
want to never or always allow cookies.